
Need GPUs? Ship without a waitlist.
Get started
As businesses expand globally, the need to balance innovation with data privacy is growing. But this growth faces rising challenges as countries and regions impose stricter rules to protect citizens' data. That’s why we see more regulations like the EU's GDPR and data-transfer rulings like Schrems II.
For businesses, the challenge is how they can harness the power and scale of the global public cloud while still complying with local data laws, which are often complex and ever-changing.
The solution to this problem is sovereign cloud. It helps organizations to comply with the data governance policies of specific regions and countries. In this guide, we will explore what a sovereign cloud is, its key pillars, and why it is essential for hybrid and public clouds.
A sovereign cloud is a cloud computing infrastructure designed to help an organization meet its digital sovereignty requirements. It ensures that the data and related activities are governed by the laws of the country or region where the data is collected and processed.
A sovereign cloud provides a high degree of assurance that data is protected from foreign access. It moves away from a one-size-fits-all global model to a design that is physically, logically, and operationally aligned with jurisdictional boundaries.
Such a setup addresses concerns about cross-border government surveillance and data access laws, like the U.S. CLOUD Act, which can require U.S.-based companies to provide data to authorities even if it is stored elsewhere.
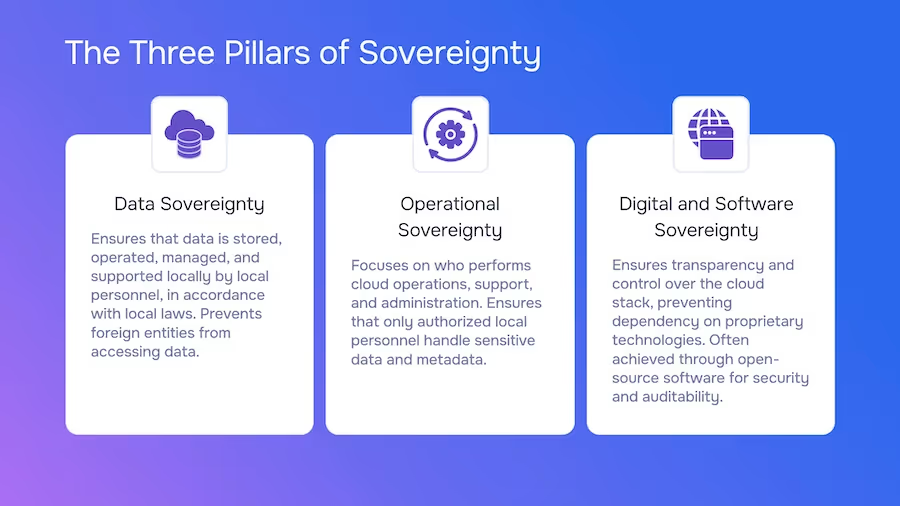
To truly be "sovereign," a cloud must stand on three strong pillars. These pillars work together to create a secure and compliant environment.
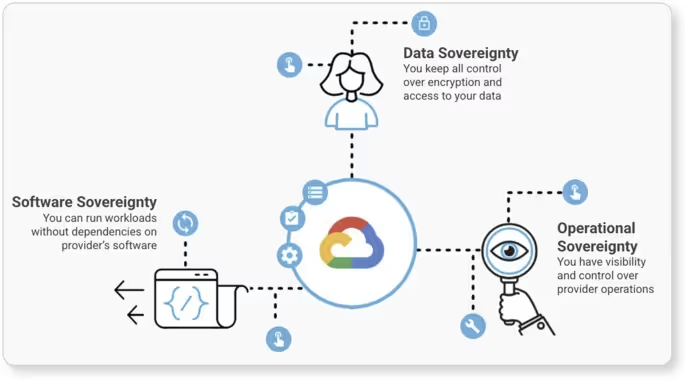
Data sovereignty mandates that data be stored, operated, managed, and supported locally by local personnel, in accordance with local laws. It ensures that no foreign entity or government can gain access to the data. Data sovereignty also dictates who can access the data, why, and under what legal rules.
Moreover, data sovereignty includes information about the data itself (metadata). This can be system logs, analytics, support tickets, or user identity details. Many regulatory frameworks consider metadata as important and sensitive as the data itself because it can reveal patterns and sensitive information.
A true sovereign cloud ensures both data and its metadata remain within the jurisdiction's legal limits.
Operational sovereignty addresses the "who" and "how" of cloud management (cloud services). It ensures that only personnel who meet certain requirements, like citizenship or security clearance (local, in-country personnel), perform operations, support, or administrative tasks. This prevents foreign entities or even provider staff from outside the jurisdiction from accessing sensitive data or metadata.
Digital and software sovereignty ensures the cloud stack itself is transparent and trustworthy. It's about avoiding "black box" technologies where you can not be sure what's happening inside. It gives you control over the software and prevents you from being "locked in" to a single vendor.
Software sovereignty is often achieved through the use of open-source software, which enables security audits and eliminates hidden "backdoors" or unauthorized data transmission. It gives the country and customer control over their technological future, so they are not dependent on a single foreign provider's proprietary code.
To clarify how each pillar contributes to cloud sovereignty, here’s an overview of the three key components.
When these three pillars are put into action, they shape the key features that define a sovereign cloud and set it apart from standard public cloud regions.
Based on those features, a fully isolated sovereign cloud might seem like the best choice. But this approach creates a new set of problems (sovereign cloud paradox). Organizations may end up limiting innovation, incurring higher costs, and facing new risks by aiming for maximum security and compliance.
To get perfect sovereignty, you risk higher costs, slower innovation, and greater vendor lock-in, which is a trade-off that most businesses would rather avoid.
So, if a pure sovereign cloud has downsides, then what is the ideal solution?
The key lies not in an "all or nothing" choice, but in creating a modern IT ecosystem that matches the appropriate cloud environment to the specific data it holds.
A hybrid model allows an organization to blend public cloud services with its own private data center. This is a key enabler for sovereignty.
The benefit: This model offers maximum data sovereignty and residency as regulated data stays within the building. And non-sensitive workloads can benefit from public cloud’s built-in redundancy and disaster recovery. Also, the organization can use a unified control plane to manage both its on-premises sovereign and public cloud workloads.
A multi-cloud strategy involves using services from multiple cloud providers. This model allows an organization to achieve "software sovereignty" (avoiding vendor lock-in) and place workloads (applications) in the environment that best suits their regulatory and business needs.
The strategic guide above shows that a sovereign cloud strategy is not about choosing a single cloud but about building a hybrid and multi-cloud architecture that balances compliance, performance, and cost. But this creates challenges in managing the complexity between cloud systems.
You get a unified cloud management platform with sovereign cloud integrations out of the box, plus a clear, centralized view of your entire hybrid and multi-cloud footprint. Instead of stitching together policies, tooling, and audits across environments, emma gives you a single operational layer built for sovereignty from day one.
A sovereign cloud strategy works best when it blends the strengths of hyperscalers with the assurances of local sovereign providers. As jurisdictional and uptime rules tighten globally, your cloud estate needs the agility to keep up.